When my uncle called in May 2021 to ask if I wanted to program for a crypto game called Dark Forest, it was an easy pass. I was saying no to the picture I had of crypto: a wasteland of financial speculation, criminal activity, and squandered energy. He tried to soothe my concerns: “Don’t worry about the scammy stuff. Porn drove the rise of the Internet, and speculators will do the same for crypto.” This wasn’t very convincing, but I was still curious to see what the hype was about. The programmer in me wanted to understand the technical underpinnings of crypto, and the political enthusiast wanted to understand why the Securities and Exchange Commision and the Chinese Communist Party were both going after what I considered a fringe libertarian project.
To my surprise, everything I touched in Dark Forest was exciting. My uncle and I started a decentralized autonomous organization (DAO) of players and conducted some novel coordination experiments. Our most famous project was a smart contract that allowed individual players to combine their points and receive a proportional amount of the prize trophy. Our code used the transparency of a blockchain to let players from all over the world verify that their contributions would be counted. On one memorable day, players from China, Spain, Australia, and Serbia flooded into our Discord server to contribute to our new collective. To me, this was proof that blockchains could be useful for organizing and coordinating across borders, not just for speculating on coins.
But speculation was still a driving force behind the popularity of the game. Venture capitalists started sending us DMs on Twitter. I was even invited to move to Hong Kong, where a “crypto whale” wanted to work with us on an East Asian version of the game. However, in May 2022, the tables turned with the infamous Terra/Luna crash, which wiped out the life savings of many and caused the value of other cryptocurrencies to nosedive. The fallout from Terra drove major crypto firms to bankruptcy and exposed Sam Bankman-Fried’s (SBF) fraudulent bookkeeping. Law enforcement stepped up as well, recovering stolen Bitcoin and placing sanctions on services that anonymize cryptocurrencies. Our game wasn’t immune to the crash either; disheartened players stopped responding in Discord and community donations dried up.
To me, this was proof that blockchains could be useful for organizing and coordinating across borders, not just for speculating on coins.
Amid the chaos, I have witnessed two extreme reactions to these events. There are the skeptics, who say this year shows why crypto is nothing but trouble; and there are the maximalists, who continue to insist that any regulation is authoritarian overreach. My past two years in crypto have shown me that both of these positions are wrong. To the skeptics, I say that crypto is innovative and necessary, and to the maximalists, I say that there are legitimately harmful uses of the technology that need to be curtailed. To understand my position, we must start from the basic principles underlying the technology.
Why crypto(graphy) matters
Before crypto came to mean cryptocurrency, it referred to the mathematical field of cryptography. Cryptography has a long lineage, from schemes for scrambling Julius Caesar’s secret messages to the German Enigma machine in World War II, but we’ll pick up the story with the invention of asymmetric encryption in the 1970s. In asymmetric cryptography, two different “keys” are generated: a public key and a private key. The public key is made widely available to others, while the private key is kept secret and known only to the owner. The keys are mathematically related in such a way that data encrypted with one key can only be decrypted with the corresponding key from the pair. Furthermore, it is computationally infeasible to derive the private key from a public key. A typical private key is 256 bits, which means an adversary would have to roll the dice 2256 times to be sure of finding the key. To put this number in perspective, a computer that could do one billion dice rolls per second would still require more time than the current age of the universe to check every key.
In a world where governments have orders of magnitude more resources than ordinary citizens, asymmetric cryptography stands out as a tool that treats all people equally.
In many systems, both physical and digital, an attacker has an easier job than a defender, because a defender must defend against every possible attack at all times. We remember the Trojan Horse, not the ten previous years the Greeks spent trying to break into Troy. Asymmetric cryptography, in contrast, is one of the few systems where the defenders have a massive advantage. If I encrypt a message with my friend’s public key, I know with near certainty that only my friend will be able to decrypt its contents, using her private key. Anyone wanting to access that message, including the government or military, would have to steal my friend’s private key from her computer or compel her to share it with them. This is quite possible, of course, but it requires more effort than simply scanning the messages of millions of people à la NSA. In a world where governments have orders of magnitude more resources than ordinary citizens, asymmetric cryptography stands out as a tool that treats all people equally.
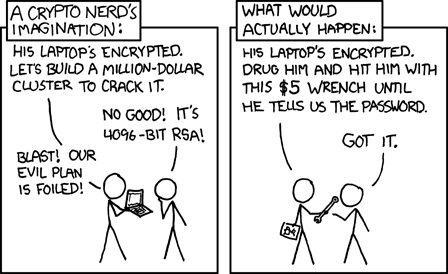
Bitcoin’s primary innovation was to make possible a database of information with the same fundamental property as asymmetric cryptography: It is significantly easier to maintain and defend than it is to attack or corrupt. This property is achieved by offering economic incentives for honest participants, and building in extreme redundancy by having every computer in the network maintain its own copy of the database. This database looks like a chain of transactions — a blockchain — where each new transaction contains a reference to the ones that came before it.1
Blockchains created the ability to have digital scarcity, to ensure that a certain piece of data is unique. Although file sharing is at the heart of the Internet, there are objects which cannot be copied without limit. Social Security numbers, votes, and money are some examples where scarcity is necessary. This is different from artificial scarcity, often seen in luxury goods like Birkin bags, whose supply is intentionally constrained to increase demand. Bitcoin, the blockchain, enforces digital scarcity for bitcoins, the cryptocurrency. There is a clear protocol for when new bitcoins are minted and they cannot be duplicated. Over time, bitcoins grew in value as people realized that they could trust Bitcoin to accurately track the ownership and supply of bitcoins.
A few years later, Ethereum was born out of a realization: instead of just storing a ledger for bitcoins on a blockchain, you could also store and interact with computer programs. A transaction previously consisted of sending money from person A to person B, but now person A could interact with program C. These programs are called smart contracts, because they are agreements (contracts) that can enforce themselves (smart). A popular analogy for a smart contract is a vending machine: If you give me one dollar and press A2, I will give you Swedish Fish. Once the dollar is received, the machine gives out the candy on its own. Smart contract agreements extend far beyond purchases, such as If you are a member of this club, you can vote and If you contribute points to the team, you will be rewarded. Anyone who is skeptical of the proposed agreement can examine the code and verify the logic for themselves, although this does require some technical knowledge.
These new cryptographic tools provide a crucial check on the increasing concentration of power in our institutions, lower the barrier for people around the world to work together, and are sometimes just a more efficient way of doing things. With cryptocurrencies and smart contracts, people can directly exchange or store value and enforce agreements with a similar degree of protection as sending encrypted messages. We can now send money to anyone in the world without central bank approval and create binding, trans-national agreements without a legal system. When Paypal, under pressure from the U.S. government, cut off payments to the watchdog organization WikiLeaks, donors could instead use Bitcoin to send their support. In 2019, when Argentina prevented its citizens from buying more than $200 U.S. dollars per month, people purchased stablecoins (a cryptocurrency designed to avoid volatile price swings) rather than keep their earnings in devalued pesos. The uses of smart contracts include the ability to take out a loan without a traditional credit score and transparent governance systems for voting and budget approval.
To fully realize the benefits of smart contracts and cryptocurrencies, we must also be prepared to deal with the antisocial uses of these tools as well. There is a strong political tradition in crypto that opposes regulation of any kind, stemming in part from the anti-state position of Bitcoin’s early adopters. My view, on the other hand, is that because crypto has been and will continue to be abused by bad actors, we need a viable regulatory framework.
Why regulation matters
There is a fundamental tension between the autonomy of an individual and the health of a collective, especially when the individual’s actions affect people other than themselves. For example, there can be the right to bear arms, but mass shootings cause intense pain and suffering to entire communities. The primary double-edged sword with cryptocurrencies and blockchains concerns financial privacy.
Basic financial privacy is a good thing, but complete financial privacy enables a host of antisocial behavior from money laundering to tax evasion. Our laws address this tension by mandating privacy in personal banking, but still allowing the IRS to access records during audits. We are still figuring out the legal framework for privacy on blockchains, but important steps forward were taken this year.
It is actually difficult to hide financial records on blockchains. The history of every transaction is public, so if a wallet receives stolen funds, law enforcement knows that wallet is associated with criminal activity. Centralized exchanges for swapping fiat and crypto routinely bar wallets suspected of criminal activity from transacting. In a famous case, a couple that stole over five billion dollars’ worth of Bitcoin were caught six years later; they never managed to launder their money through an exchange. Their wallets were so tainted that they resorted to buying Walmart gift cards and gold, a tactic that resulted in their capture.
On Ethereum, it’s possible to implement a service called a “mixer.” These are smart contracts that enable users to deposit funds from one wallet into a common pool, and then withdraw the same amount from the pool into another wallet — with no direct link between the two. This provides financial privacy for users who don’t want their complete financial history visible to everyone, but also enables money laundering. The most popular mixer is called Tornado Cash (TC), and it was used by a North Korean hacker group to anonymize over $400 million in stolen funds. In August of 2022, the US Office of Foreign Asset Control announced that US residents could no longer use the service, and that any wallet that interacted with TC moving forward would be flagged as suspicious.
The Tornado Cash sanctions demonstrate the ability to mitigate antisocial behavior while still maintaining the strong guarantees that crypto provides for individual rights. Although the TC smart contract cannot be taken down directly,2 ordinary users stopped using the service because, for most of them, there was a direct link between their bank account and their crypto wallets.3 This made the mixer less effective, because privacy depends on a large pool of potential withdrawers. For users still seeking privacy, developers proposed modifications to TC — such as Know Your Customer requirements and deposit limits — that resemble safeguards in the traditional banking system. The key difference, however, is that users prove they are not on a list of flagged wallets in order to deposit. This proof keeps the user’s identity private, while verifying that their activity is licit. Individuals still have financial privacy tools at their disposal that the government cannot take away, but criminals laundering large sums of money can no longer hide behind law-abiding users.
Looking forward
Speculators, cover your ears: the market crash and sanctions of the past year have been good for crypto. VCs are leaving, frauds like SBF have been exposed, and regulation is starting to reign in antisocial behavior. The honeymoon phase of “crypto will make everyone rich and remove the need for governments” is over. Instead, we are figuring out where crypto can enhance existing functions in society (voting), provide viable alternatives (stablecoins in the face of devaluation), and create new mediums for Internet-scale coordination (Dark Forest).
Beyond the technology’s specific use cases, crypto has a set of values — equality, transparency, access, and privacy — that set higher standards for our politics and institutions. Many human organizations in the crypto space are starting to reflect the qualities of the technology they are building on: All of the Ethereum code is open-source, meetings discussing network upgrades are public, and privacy is respected by allowing people to apply for jobs under their online handles.
Crypto has a set of values — equality, transparency, access, and privacy — that set higher standards for our politics and institutions.
I see a potential future where we demand similar practices from institutions outside of the crypto world. In turn, our governments, banks, and courts would become more accountable to the people they serve, and earn the people’s trust. Nations could also rely on the neutral base layer of Ethereum to create and enforce agreements between themselves, facilitating coordination and enabling political projects on the global scale needed to combat climate change. This might be a long shot — but so was Ethereum.
Notes
Footnotes
-
Blockchain security originally required tons of computation, which meant massive amounts of electricity had to be expended. But new protocols have reduced network energy consumption by 99.99 percent. ↩
-
It would cost around $4.6 billion per attempt to attack the network, and even then, the best an attacker could do is refuse to allow any new transactions to interact with Tornado Cash. Users could upload new copies of the contract and migrate their funds, but that would create an expensive game of cat and mouse. ↩
-
The exchange where they used fiat currency to buy crypto can link a user’s bank account to their crypto wallet, and provide that data to a government when subpoenaed. ↩
Author
Tony
Tony is a freelance software engineer based in Seattle, Washington. He studied politics and computer science at Tufts, and believes both fields have a lot to learn from each other. In his free time, he plays pro ultimate frisbee and reads manifestos.
Editor
Marc Shkurovich
Marc Shkurovich is an editor and writer based in Berlin. He works for The Syllabus, America's favorite knowledge discovery platform, and studies the semiotics of digital capitalist culture. Catch Marc at NYU Law starting in 2024.